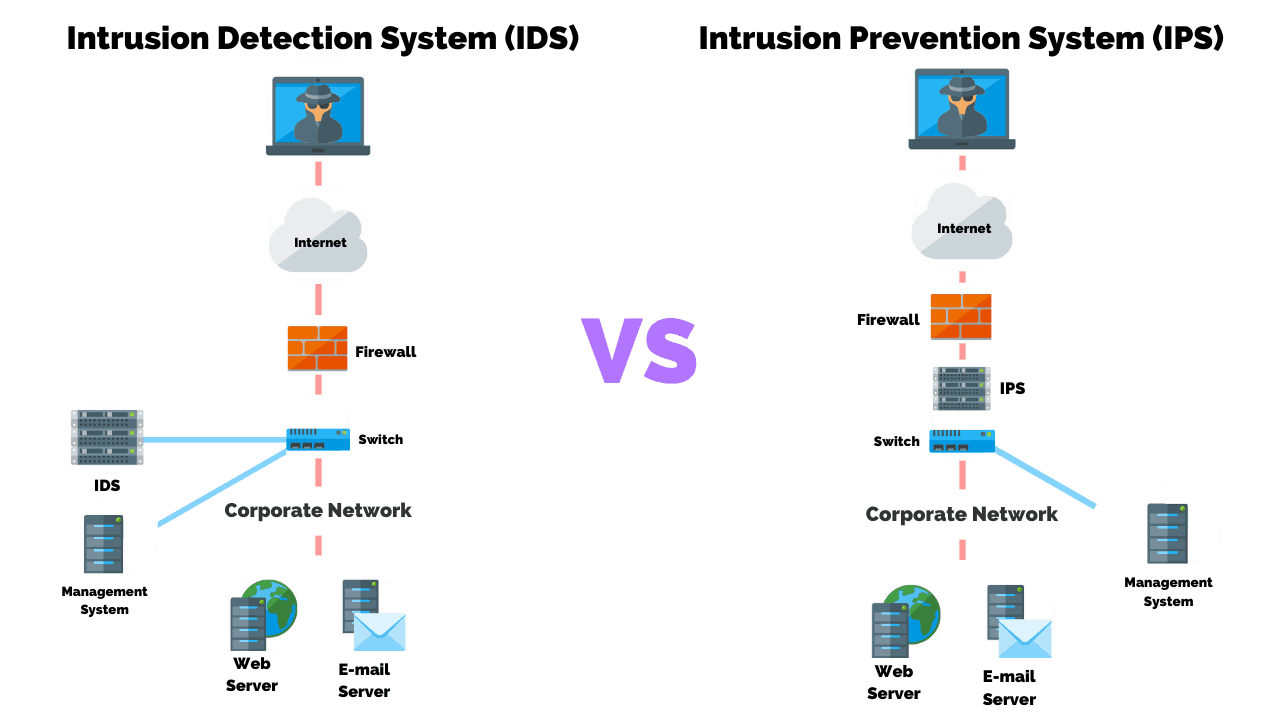
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices - Spiceworks
![Cisco Adaptive Wireless Intrusion Prevention Service Configuration Guide, Release 5.2 - Overview [Cisco Adaptive Wireless IPS Software] - Cisco Cisco Adaptive Wireless Intrusion Prevention Service Configuration Guide, Release 5.2 - Overview [Cisco Adaptive Wireless IPS Software] - Cisco](https://www.cisco.com/content/dam/en/us/td/i/200001-300000/270001-280000/273001-274000/273105.tif/_jcr_content/renditions/273105.jpg)
Cisco Adaptive Wireless Intrusion Prevention Service Configuration Guide, Release 5.2 - Overview [Cisco Adaptive Wireless IPS Software] - Cisco

Research of wireless intrusion prevention systems based on plan recognition and honeypot | Semantic Scholar